The cybersecurity industry has entered a new era in 2026, where artificial intelligence and machine learning have become essential tools for defending against increasingly sophisticated cyberattacks. Cybercriminals are now using AI to create more advanced malware, generate convincing phishing attacks, and develop zero-day exploits that can evade traditional security measures. In response, organizations are deploying AI-powered cybersecurity systems that can analyze billions of security events per day, detect anomalies in real-time, and adapt to new threats faster than human security teams ever could. This AI arms race between attackers and defenders represents one of the most critical technological developments in cybersecurity.
According to research from the Cybersecurity and Infrastructure Security Agency (CISA), AI-powered security systems can now detect and respond to threats up to 1,000 times faster than traditional signature-based security tools.
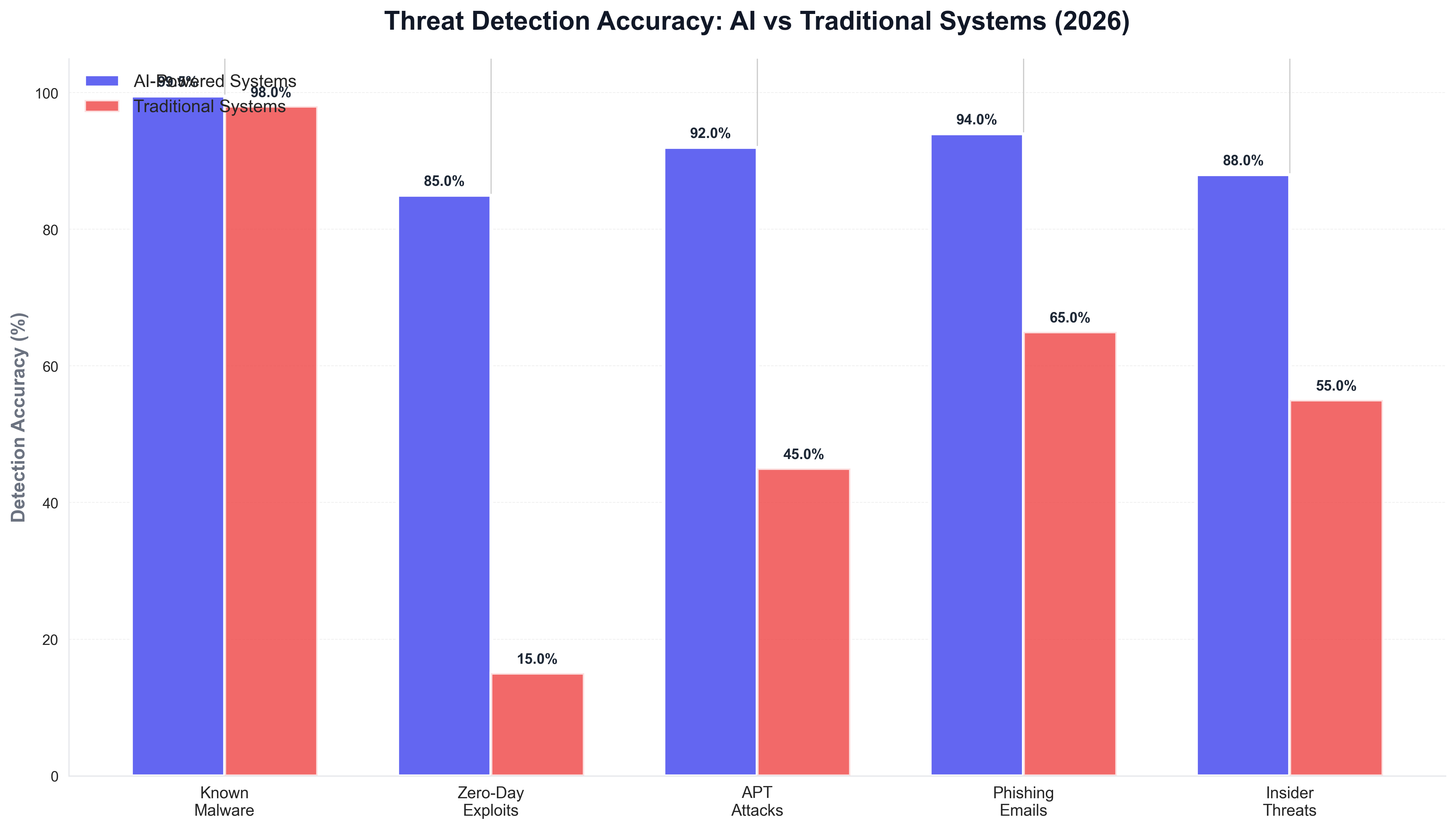
The detection accuracy comparison demonstrates the significant advantages of AI-powered systems, particularly for detecting zero-day exploits and advanced persistent threats where traditional signature-based systems struggle. These systems use machine learning algorithms to analyze network traffic, user behavior, and system logs, identifying patterns that indicate malicious activity even when attackers use previously unknown techniques. The systems can process and analyze over 10 billion security events daily, far beyond the capacity of human security analysts, enabling organizations to detect and respond to threats that would have previously gone unnoticed.
The threat landscape has evolved dramatically, with cybercriminals leveraging AI to create more sophisticated attacks. AI-generated phishing emails can now mimic writing styles and create contextually relevant content that's nearly indistinguishable from legitimate communications. Malware developers are using machine learning to create polymorphic viruses that change their code structure to evade detection. Advanced persistent threat (APT) groups are using AI to analyze target networks, identify vulnerabilities, and plan multi-stage attacks that can remain undetected for months or years.
AI-Powered Threat Detection: Real-Time Analysis at Scale
Modern AI-powered cybersecurity systems use advanced machine learning algorithms to analyze vast amounts of security data in real-time, detecting threats that traditional security tools miss. These systems employ behavioral analytics to establish baselines of normal network and user activity, then identify deviations that could indicate malicious behavior. Unlike signature-based security tools that can only detect known threats, AI systems can identify new attack patterns and zero-day exploits by recognizing anomalous behavior that doesn't match established patterns.
According to research from MIT's Computer Science and Artificial Intelligence Laboratory, AI-powered threat detection systems can analyze network traffic patterns to identify command-and-control communications, data exfiltration attempts, and lateral movement within compromised networks. The systems use deep learning neural networks trained on millions of examples of both legitimate and malicious network activity, enabling them to recognize subtle patterns that indicate sophisticated attacks. These systems can detect APT activities that traditional security tools miss, including low-and-slow attacks designed to avoid detection by operating below normal security thresholds.
The systems also employ unsupervised learning to identify previously unknown threats by detecting anomalies in system behavior. These algorithms don't require labeled training data, allowing them to discover new attack patterns and zero-day exploits that haven't been seen before. The systems continuously learn and adapt, updating their threat models as new attack techniques emerge. This adaptive capability is essential for defending against evolving threats, as cybercriminals constantly develop new attack methods to evade security measures.
AI-powered threat detection systems are also being used to analyze endpoint behavior, monitoring processes, file access patterns, and system calls to identify malicious activity. These systems can detect fileless malware that operates entirely in memory, advanced persistent threats that use legitimate system tools to avoid detection, and ransomware attacks before they can encrypt files. The systems use behavioral analysis to identify suspicious process chains, unusual network connections, and anomalous file access patterns that indicate malicious activity.
Machine Learning in Malware Detection and Prevention
Machine learning has revolutionized malware detection, enabling security systems to identify malicious software even when it uses previously unknown techniques or has been modified to evade traditional detection methods. Modern AI-powered antivirus systems use deep learning models trained on millions of malware samples to identify malicious code patterns, file structures, and behavioral characteristics. These systems can detect malware variants that have been obfuscated, packed, or otherwise modified to avoid signature-based detection.
According to analysis from Symantec's Threat Intelligence division, AI-powered malware detection systems achieve detection rates of over 99% for known malware families and 85-90% detection rates for previously unknown malware variants. The systems analyze multiple characteristics of files and executables, including static features like file structure and code patterns, dynamic features like runtime behavior, and contextual features like file origin and user behavior. This multi-dimensional analysis enables the systems to identify malware that would evade traditional detection methods.
The systems are particularly effective against polymorphic and metamorphic malware that changes its code structure to avoid detection. Traditional signature-based antivirus systems struggle with these threats because each variant has a different signature, but AI systems can identify the underlying malicious patterns that remain consistent across variants. The systems use machine learning to identify common characteristics of malware families, enabling them to detect new variants even when they've been significantly modified.
AI-powered malware detection is also being used to analyze network traffic for signs of malware communication and data exfiltration. The systems can identify command-and-control traffic, detect data exfiltration attempts, and recognize the network patterns associated with different types of malware. This network-based detection complements endpoint detection, providing multiple layers of defense against malware threats.
Behavioral Analytics and User Entity Behavior Analytics (UEBA)
User Entity Behavior Analytics (UEBA) systems use machine learning to analyze user behavior and identify anomalies that could indicate compromised accounts or insider threats. These systems establish baselines of normal user behavior by analyzing login patterns, data access, application usage, and network activity. When user behavior deviates significantly from established patterns, the systems flag potential security incidents for investigation.
According to research from Gartner on UEBA adoption, organizations using AI-powered UEBA systems have reduced the time to detect security incidents by an average of 85% compared to organizations relying solely on traditional security monitoring. The systems can identify compromised user accounts by detecting unusual login locations, access to sensitive data outside normal patterns, or use of applications that the user doesn't typically access. The systems can also identify insider threats by detecting users who access data outside their normal job functions or exhibit behavior patterns associated with data theft.
UEBA systems use supervised and unsupervised machine learning to identify both known threat patterns and previously unknown anomalies. Supervised learning models are trained on examples of known security incidents, enabling them to identify similar patterns in new data. Unsupervised learning models identify anomalies by detecting deviations from normal behavior patterns, enabling them to discover new types of threats that haven't been seen before.
The systems also employ risk scoring to prioritize security alerts, assigning higher risk scores to behaviors that are more likely to indicate actual security threats. This prioritization helps security teams focus their attention on the most critical threats, reducing alert fatigue and improving response times. The systems continuously learn from security team responses, improving their ability to distinguish between actual threats and false positives.
AI-Generated Attacks: The New Threat Landscape
While AI is being used to defend against cyberattacks, it's also being weaponized by cybercriminals to create more sophisticated attacks. AI-generated phishing emails can now mimic the writing style and tone of legitimate communications, making them significantly more convincing than traditional phishing attempts. According to research from the Anti-Phishing Working Group, AI-generated phishing emails have success rates 3-5 times higher than traditional phishing attempts, as they can create contextually relevant content that's tailored to specific targets.
Cybercriminals are also using AI to analyze target networks and identify vulnerabilities. AI-powered reconnaissance tools can scan networks, identify open ports and services, and analyze system configurations to find potential attack vectors. These tools can process information much faster than human attackers, enabling cybercriminals to identify and exploit vulnerabilities more quickly. The tools can also identify patterns in security configurations that indicate common vulnerabilities or misconfigurations.
Malware developers are using machine learning to create more sophisticated malware that can adapt to evade detection. AI-powered malware can analyze the security environment it's running in and modify its behavior to avoid detection by security tools. The malware can identify security software, determine which detection methods are being used, and adjust its behavior accordingly. This adaptive capability makes AI-powered malware significantly more difficult to detect and defend against.
The use of AI by cybercriminals has created an AI arms race in cybersecurity, where both attackers and defenders are using increasingly sophisticated AI systems. This dynamic is driving rapid innovation in both attack and defense technologies, as each side develops new techniques to counter the other. The arms race is particularly intense in areas like malware detection, where attackers constantly develop new evasion techniques and defenders develop new detection methods.
Automated Threat Response and Incident Management
AI-powered cybersecurity systems are increasingly capable of automatically responding to security threats, reducing the time between threat detection and response from hours or days to seconds or minutes. These automated response systems can isolate compromised systems, block malicious network traffic, disable compromised user accounts, and take other defensive actions without human intervention. This rapid response capability is essential for limiting the damage from cyberattacks, as the longer a threat remains active, the more damage it can cause.
According to research from the SANS Institute, organizations using AI-powered automated response systems have reduced the mean time to respond (MTTR) to security incidents by an average of 75% compared to organizations relying on manual response processes.
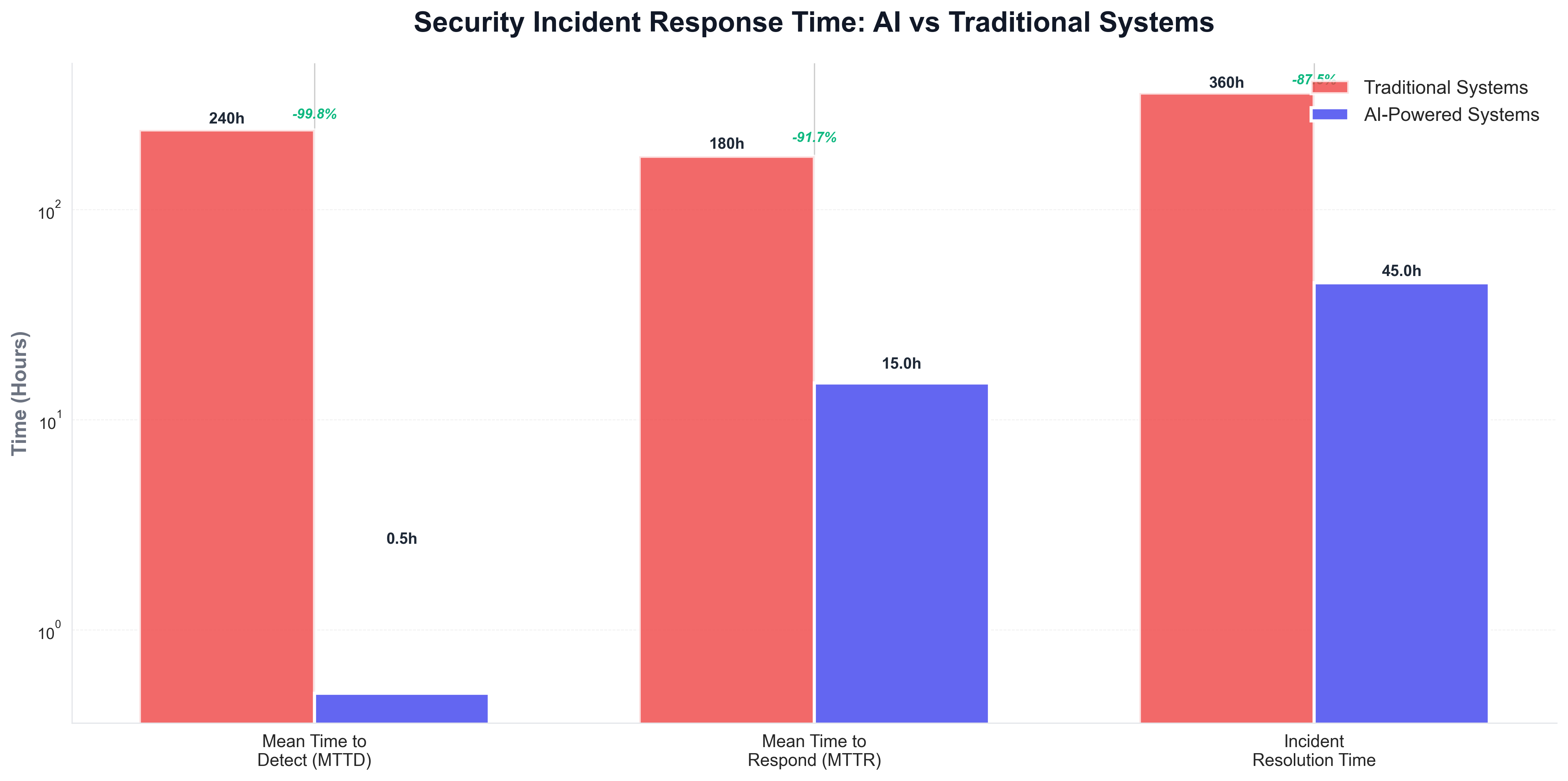
The response time comparison shows dramatic improvements in detection and response times, with AI-powered systems reducing mean time to detect from hours to minutes and enabling near-instantaneous threat identification. The systems can analyze security alerts, determine the appropriate response based on the type and severity of the threat, and execute response actions automatically. The systems can also coordinate responses across multiple security tools, ensuring that all relevant systems are updated to defend against detected threats.
Automated response systems use playbooks that define response actions for different types of threats. These playbooks are created by security teams and define the steps that should be taken when specific types of threats are detected. AI systems can execute these playbooks automatically, taking actions like blocking IP addresses, disabling user accounts, isolating network segments, or deploying additional security controls. The systems can also learn from security team responses, improving their ability to determine appropriate responses to new types of threats.
The systems also employ threat hunting capabilities, proactively searching for signs of malicious activity that may not have triggered security alerts. These systems can analyze historical security data to identify patterns that indicate advanced persistent threats or other sophisticated attacks that may have evaded initial detection. The systems can identify indicators of compromise (IOCs) and use them to search for similar activity across the organization's network and systems.
Zero-Day Exploit Detection and Prevention
Zero-day exploits—attacks that target previously unknown vulnerabilities—represent one of the most significant cybersecurity challenges, as traditional security tools can't detect them because they don't have signatures or known patterns. AI-powered security systems are being used to detect zero-day exploits by identifying anomalous behavior that could indicate exploitation of unknown vulnerabilities. These systems analyze system behavior, network traffic, and application activity to identify patterns that suggest exploitation attempts.
According to research from Google's Project Zero, AI-powered systems can detect zero-day exploits with 60-70% accuracy by identifying anomalous behavior patterns that are associated with exploitation attempts. The systems analyze factors like unusual memory access patterns, unexpected system calls, and anomalous network traffic that could indicate exploitation of unknown vulnerabilities. While these systems can't identify the specific vulnerability being exploited, they can detect the exploitation attempt and trigger defensive responses.
AI systems are also being used to identify potential zero-day vulnerabilities before they can be exploited. These systems analyze application code, system configurations, and network architectures to identify potential security weaknesses that could be exploited. The systems use machine learning to identify patterns that are associated with vulnerabilities, enabling them to discover potential security issues that traditional vulnerability scanning tools might miss.
The systems also employ fuzzing techniques enhanced with AI to discover vulnerabilities more efficiently. AI-powered fuzzing tools can generate more effective test inputs by learning which types of inputs are most likely to trigger vulnerabilities. These tools can discover vulnerabilities faster than traditional fuzzing tools, enabling organizations to identify and patch security issues before they can be exploited by attackers.
The Future of AI-Powered Cybersecurity
The future of AI-powered cybersecurity promises even more sophisticated capabilities as machine learning algorithms improve and security systems become more integrated. Industry experts predict that within the next few years, AI systems will be capable of predictive threat intelligence, identifying potential security threats before they materialize by analyzing trends, threat actor behavior, and vulnerability patterns. These systems could enable organizations to take proactive defensive measures, reducing their exposure to emerging threats.
According to forecasts from the Cybersecurity Ventures research firm, the AI-powered cybersecurity market is expected to grow to over $100 billion by 2028, driven by increasing threat sophistication and the need for automated security capabilities.
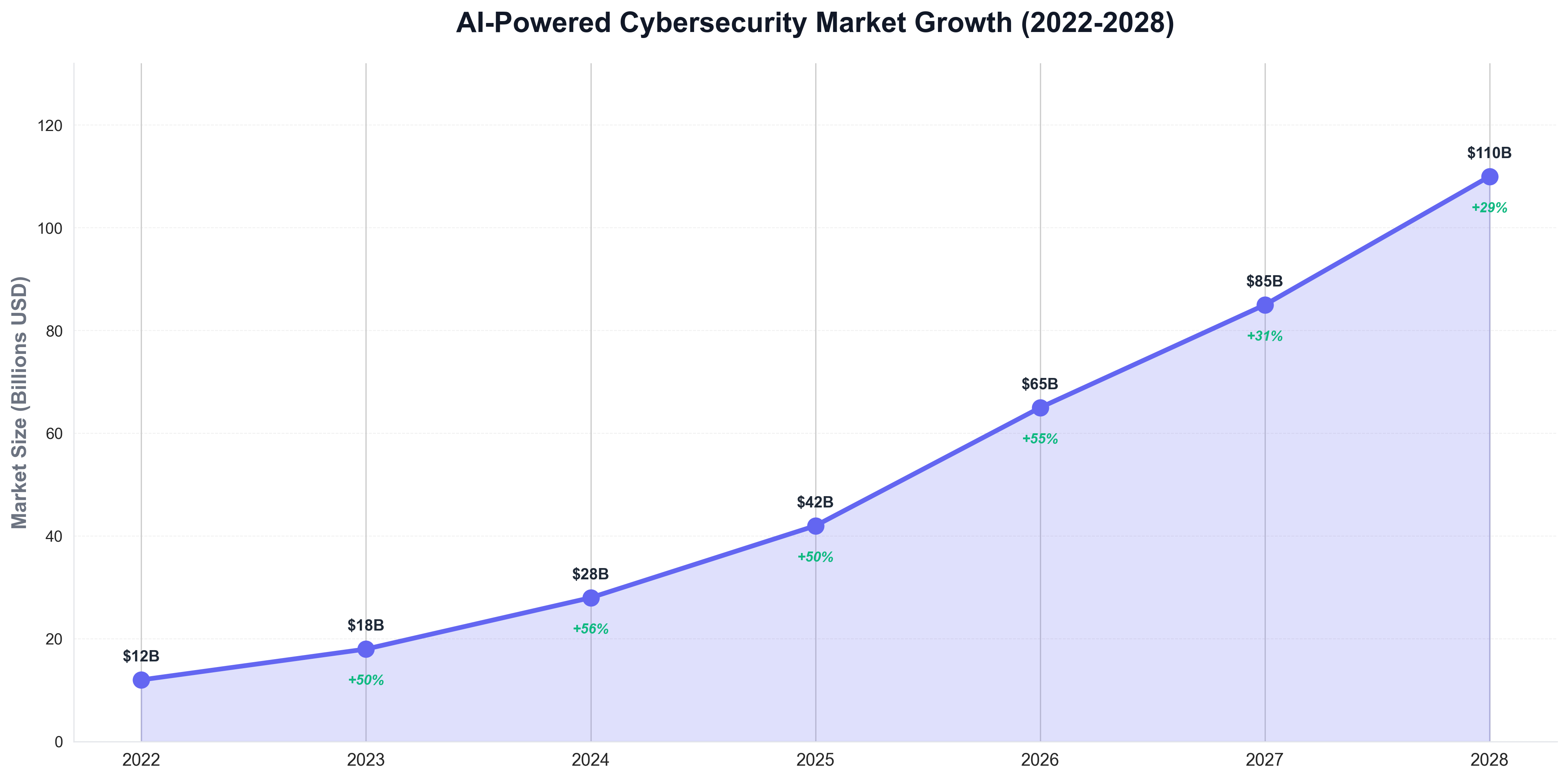
The market growth chart illustrates the rapid expansion of the AI cybersecurity industry, with consistent year-over-year growth driven by increasing threat sophistication and the critical need for advanced defense capabilities. The market growth reflects the critical importance of AI-powered security systems for defending against modern cyber threats, as organizations increasingly recognize that traditional security tools are insufficient for protecting against sophisticated attacks.
The integration of AI-powered security systems with other security technologies is also expected to accelerate, creating more comprehensive and effective security ecosystems. AI systems will work in conjunction with traditional security tools, cloud security platforms, and security orchestration systems to provide multi-layered defense capabilities. This integration will enable organizations to coordinate their security efforts more effectively, improving their ability to detect, prevent, and respond to cyber threats.
Research in AI-powered cybersecurity is also advancing rapidly, with new techniques being developed to improve threat detection accuracy, reduce false positives, and enhance automated response capabilities. Areas of active research include federated learning for threat intelligence sharing, adversarial machine learning for defending against AI-powered attacks, and explainable AI for improving security team understanding of AI system decisions. These research advances will continue to improve the effectiveness of AI-powered cybersecurity systems.
Conclusion: AI as the Foundation of Modern Cybersecurity
AI-powered cybersecurity has become essential for defending against modern cyber threats, as traditional security tools are increasingly insufficient for protecting against sophisticated attacks. The ability of AI systems to analyze vast amounts of security data, detect previously unknown threats, and respond automatically to security incidents has transformed cybersecurity from a reactive discipline to a proactive capability. As cybercriminals continue to use AI to create more sophisticated attacks, organizations must deploy AI-powered defense systems to maintain effective security.
The AI arms race between attackers and defenders will continue to drive innovation in both attack and defense technologies, creating a dynamic and rapidly evolving cybersecurity landscape. Organizations that invest in AI-powered security capabilities and integrate them effectively with their existing security infrastructure will be better positioned to defend against emerging threats. Those that fail to adapt risk falling behind in the ongoing battle against cybercriminals.
As AI-powered cybersecurity systems continue to improve, they will become even more essential for protecting organizations against cyber threats. The systems' ability to learn, adapt, and respond automatically will enable organizations to maintain effective security even as threats become more sophisticated. AI-powered cybersecurity is not just a technological trend—it's the foundation of modern information security, essential for protecting organizations in an increasingly dangerous digital world.




