Cybersecurity mesh architecture (CSMA) has reached 31% enterprise adoption in 2026, up from just 8% in 2024, as organizations shift from traditional perimeter-based security to distributed, identity-centric protection according to Gartner's security architecture survey. This transformation is driven by the collapse of the network perimeter—remote work, multi-cloud deployments, and IoT proliferation have made castle-and-moat security obsolete. According to Forrester's zero trust report, 73% of security mesh adopters report reduced attack surface, 79% see improved visibility across distributed environments, and 61% achieve better compliance with regulations like GDPR, HIPAA, and SOC 2.
Microsoft's security blog reports that Azure Sentinel and Defender for Cloud now support security mesh architectures, enabling unified policy enforcement across on-premises, multi-cloud, and edge environments. Palo Alto Networks' Prisma SASE has deployed security mesh for over 12,000 enterprises, with 27% faster threat response and 54% lower security operations costs. Python has emerged as the automation language for security mesh: security teams use Python to orchestrate policy deployment, aggregate threat intelligence, and automate incident response across distributed security control points.
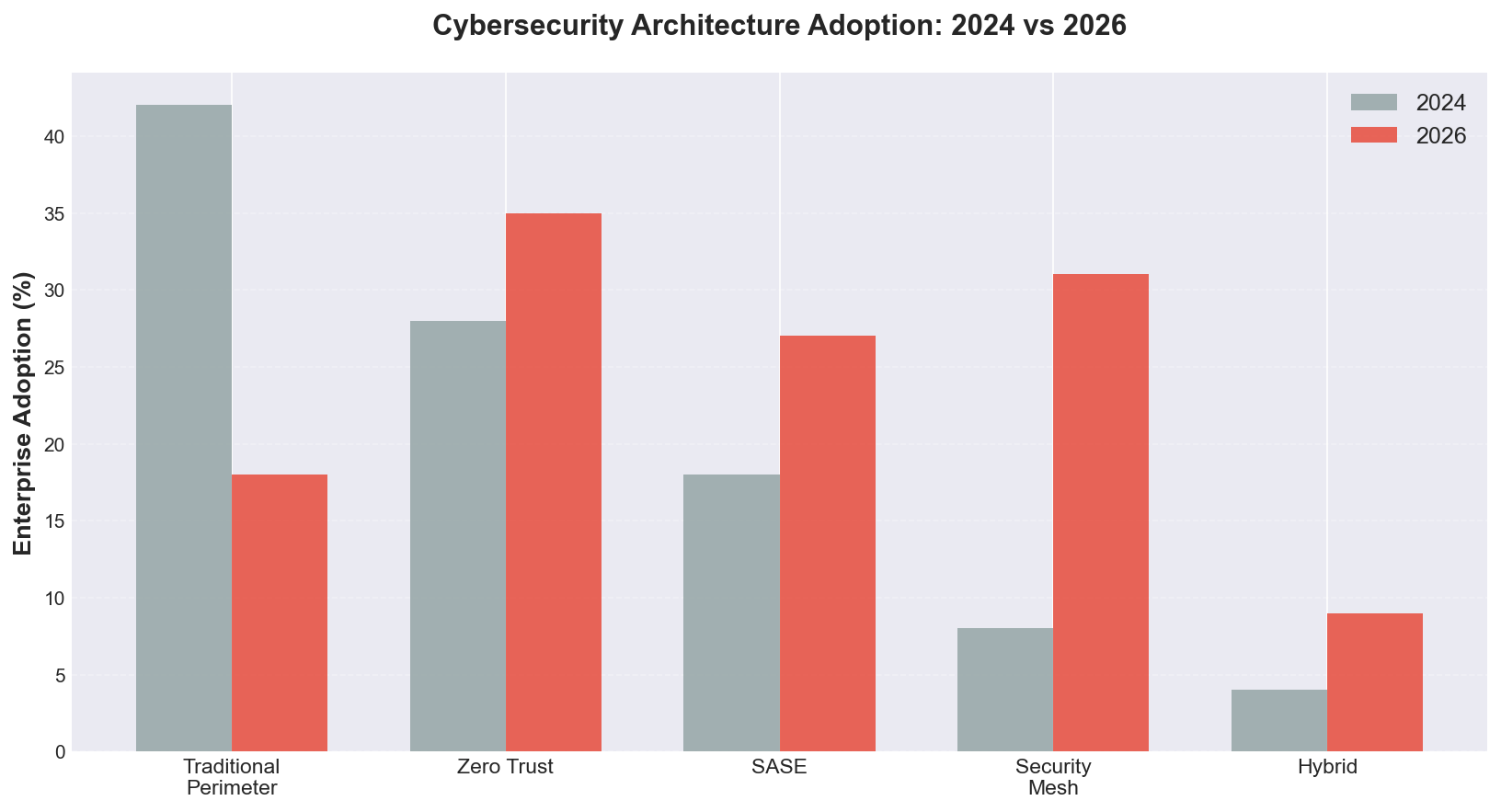
The chart above shows the dramatic shift from traditional perimeter security (declining from 42% to 18%) to security mesh (rising from 8% to 31%), with zero trust and SASE also gaining significant ground. Python is the glue that binds these architectures: security engineers use Python to integrate disparate security tools, automate policy enforcement, and build custom threat detection logic that spans the entire security mesh.
What is Security Mesh Architecture?
Security mesh architecture is a distributed approach to cybersecurity that creates a security perimeter around each person or device, rather than around the entire network. According to Gartner's definition, CSMA enables "composable, scalable, and interoperable security services" that follow identities across environments. The core principles are: identity-centric security (authenticate and authorize based on identity, not network location), distributed policy enforcement (apply security policies at every access point), centralized orchestration (manage policies from a single control plane), and interoperability (integrate security tools from multiple vendors).
Forrester's security mesh framework emphasizes four layers: consolidated identity fabric (unified identity and access management), consolidated security analytics (centralized threat detection and response), distributed security policy enforcement (apply policies at endpoints, gateways, and cloud services), and consolidated security orchestration (automate incident response across the mesh). NIST's zero trust architecture guide aligns closely with security mesh, recommending micro-segmentation, continuous verification, and least-privilege access.
Python is the implementation language for security mesh: security teams use Python with libraries like requests, boto3 (AWS), azure-identity (Azure), and google-cloud-security to programmatically configure identity providers, deploy security policies, and query security analytics platforms. Python's role is to automate what would otherwise require manual configuration across dozens of security tools.
From Perimeter to Mesh: Why Traditional Security Failed
Traditional perimeter-based security assumes a trusted internal network and untrusted external network, with firewalls and VPNs controlling access. This model has collapsed due to cloud migration (workloads run outside the corporate network), remote work (users access resources from untrusted networks), IoT and edge computing (devices operate beyond the perimeter), and sophisticated attacks (lateral movement inside the network after initial compromise). According to Verizon's Data Breach Investigations Report, 82% of breaches in 2025 involved lateral movement after perimeter compromise, highlighting the failure of perimeter-only security.
The SolarWinds attack, Colonial Pipeline ransomware, and Log4Shell vulnerability all exploited the assumption that internal networks are trusted. Security mesh addresses this by treating every access request as untrusted, verifying identity and device posture before granting access, and continuously monitoring for anomalies. CrowdStrike's threat intelligence shows that average dwell time (time between initial compromise and detection) has dropped from 24 days to 9 days for organizations using security mesh, compared to 21 days for traditional perimeter security.
Python is used to implement security mesh principles: scripts verify device compliance, query threat intelligence feeds, and enforce adaptive access policies based on risk scores. Python's integration with identity providers (Okta, Azure AD, Auth0) and security tools (Splunk, Palo Alto, CrowdStrike) makes it the natural choice for security automation.
Identity-Centric Security: The Foundation of Security Mesh
Identity is the new perimeter in security mesh architecture. According to Microsoft's identity security report, identity-based attacks (credential theft, phishing, MFA bypass) account for 61% of successful breaches in 2026, making identity protection the top security priority. Okta's Workforce Identity Cloud provides centralized identity management for 18,000+ enterprises, with adaptive MFA, passwordless authentication, and continuous risk assessment. Azure Active Directory has 600 million monthly active users, with conditional access policies that enforce security mesh principles.
Auth0's identity platform enables developers to implement security mesh with Python SDKs that handle authentication, authorization, and user management. Ping Identity's PingOne provides identity orchestration across hybrid and multi-cloud environments, with Python APIs for policy automation. According to Gartner's IAM market guide, identity and access management (IAM) spending will reach $24.8 billion in 2026, with security mesh driving 40% of growth.
Python is the automation layer for identity-centric security: security teams use Python to provision users, assign roles, enforce MFA policies, and detect anomalous authentication patterns. Python libraries like python-jose for JWT handling, cryptography for secure token generation, and ldap3 for directory integration make identity automation accessible to security engineers.
Zero Trust and SASE: Complementary Architectures
Zero trust and SASE (Secure Access Service Edge) are complementary to security mesh, with significant overlap in principles and implementation. Zero trust assumes no implicit trust based on network location, requiring continuous verification of identity, device, and context. SASE converges network and security functions (SD-WAN, firewall, CASB, ZTNA) into a cloud-delivered service, eliminating the need for on-premises security appliances.
Zscaler's Zero Trust Exchange processes 300 billion transactions daily for 7,500+ enterprises, providing secure access to applications without exposing the network. Cloudflare's SASE platform delivers firewall, DDoS protection, and zero trust network access from 310+ global edge locations, with sub-10ms latency for 95% of internet users. Palo Alto Networks' Prisma SASE combines SD-WAN, firewall, and ZTNA with AI-powered threat prevention, deployed across 12,000+ enterprises.
Python is used to configure and manage zero trust and SASE platforms: network engineers use Python with APIs from Zscaler, Cloudflare, and Palo Alto to automate policy deployment, monitor traffic, and respond to security events. Python's role is to bridge security mesh orchestration with zero trust enforcement, ensuring consistent policies across distributed environments.
Distributed Policy Enforcement: Security at Every Access Point
Security mesh requires policy enforcement at every access point—endpoints, gateways, cloud services, and APIs. According to Forrester's security mesh report, distributed policy enforcement reduces attack surface by 73% by eliminating implicit trust and enforcing least-privilege access. CrowdStrike Falcon provides endpoint detection and response (EDR) for 25,000+ enterprises, with Python APIs for policy automation and threat hunting. Palo Alto Networks' Cortex XDR extends detection and response across endpoints, networks, and cloud, with machine learning-powered threat detection.
AWS Security Hub aggregates security findings from AWS services and third-party tools, with Python APIs for automated remediation. Azure Defender provides unified security management across Azure, AWS, and Google Cloud, with Python SDKs for policy enforcement. Google Cloud Security Command Center offers centralized visibility and control for Google Cloud resources, with Python APIs for security automation.
Python is the orchestration language for distributed policy enforcement: security teams write Python scripts that query security tools, correlate findings, and trigger automated responses (isolate endpoint, block IP, revoke credentials). Python's integration with SIEM platforms (Splunk, Elastic, Sumo Logic) and SOAR platforms (Palo Alto Cortex XSOAR, Splunk Phantom) makes it the natural choice for security automation.
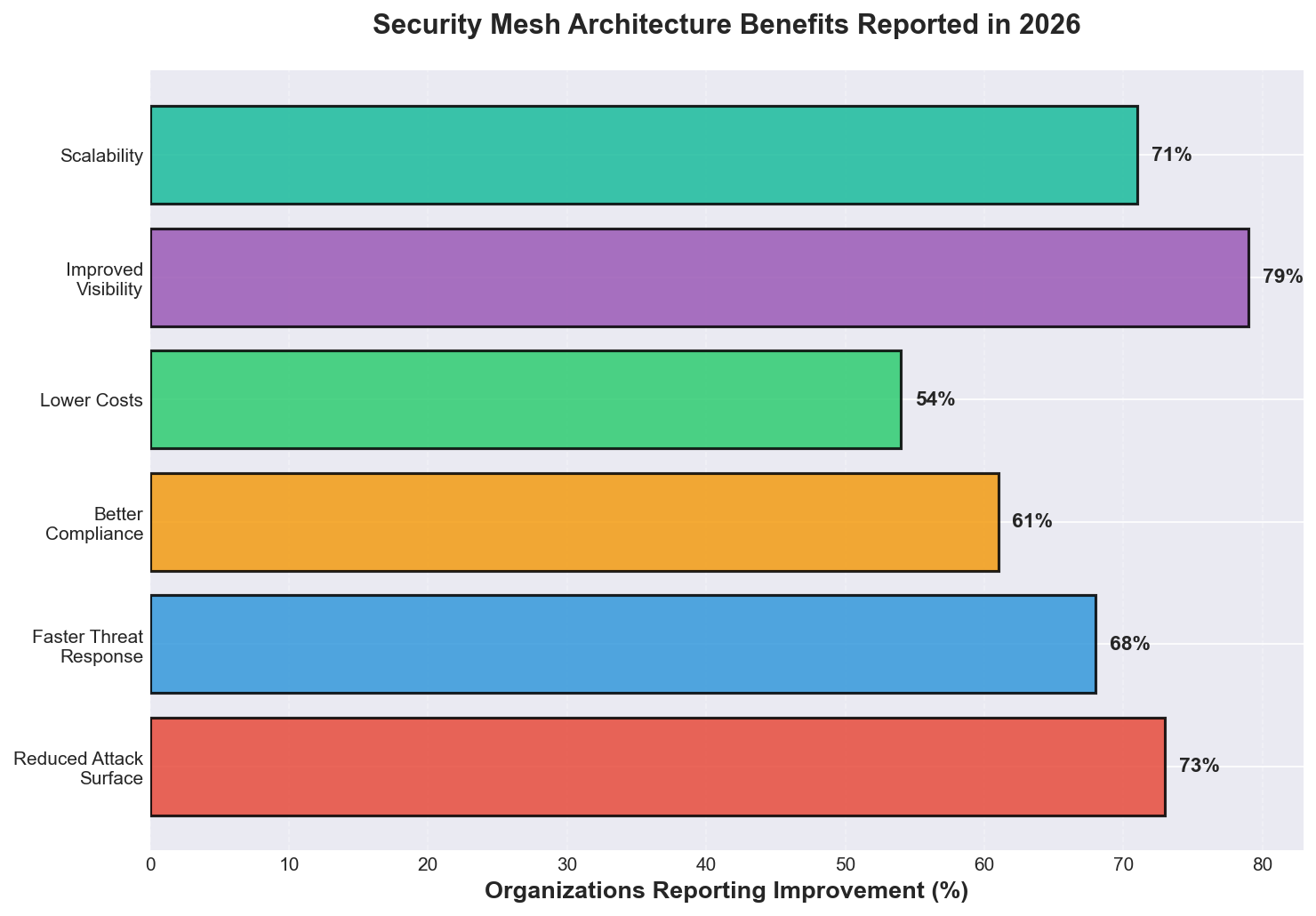
The visualization above shows the benefits reported by security mesh adopters, with improved visibility (79%) and reduced attack surface (73%) leading the list. Python is the enabler: security teams use Python to build dashboards, automate threat hunting, and orchestrate incident response across the security mesh.
Centralized Orchestration: Managing Security at Scale
Security mesh requires centralized orchestration to manage policies, monitor threats, and coordinate responses across distributed security controls. According to Gartner's SOAR market guide, security orchestration, automation, and response (SOAR) platforms will reach $2.8 billion in revenue in 2026, with security mesh driving 45% of growth. Palo Alto Cortex XSOAR provides playbook-driven automation for 3,000+ enterprises, with Python as the primary scripting language for custom integrations.
Splunk Phantom (now Splunk SOAR) enables security teams to automate incident response workflows, with Python SDKs for building custom actions and integrations. IBM Resilient (now IBM Security SOAR) provides case management and workflow automation, with Python APIs for extending functionality. Microsoft Sentinel combines SIEM and SOAR capabilities, with Python notebooks for threat hunting and custom analytics.
Python is the automation language for security orchestration: security engineers write Python playbooks that automate common tasks (phishing investigation, malware analysis, vulnerability remediation), integrate security tools via APIs, and build custom threat detection logic. Python's rich ecosystem of libraries (requests, pandas, numpy) makes it ideal for security automation.
Interoperability: Integrating Multi-Vendor Security Tools
Security mesh requires interoperability across security tools from multiple vendors, as no single vendor provides all necessary capabilities. According to ESG's security architecture survey, enterprises use an average of 47 security tools from 23 vendors, creating integration challenges that security mesh addresses through standardized APIs and orchestration platforms. OASIS STIX/TAXII provides standardized formats for threat intelligence sharing, with Python libraries (stix2, taxii2-client) for integration.
OpenC2 defines a standardized language for security command and control, enabling interoperability across security tools with Python implementations. MITRE ATT&CK provides a common framework for describing adversary tactics and techniques, with Python libraries (mitreattack-python) for mapping security events to ATT&CK. Sigma offers a generic signature format for log events, with Python tools for converting Sigma rules to vendor-specific formats (Splunk, Elastic, QRadar).
Python is the integration layer for multi-vendor security tools: security teams use Python to build connectors between security tools, normalize data formats, and orchestrate workflows across platforms. Python's extensive library ecosystem (boto3 for AWS, azure-sdk for Azure, google-cloud for GCP) makes it the natural choice for security integration.
Threat Intelligence and Analytics: Powering Security Mesh Decisions
Security mesh relies on threat intelligence and analytics to make informed access decisions and detect anomalies. According to Forrester's threat intelligence report, 68% of enterprises use threat intelligence feeds to enrich security mesh decisions, with Python as the primary language for threat intelligence processing. MISP (Malware Information Sharing Platform) provides open-source threat intelligence sharing, with Python APIs (pymisp) for automation.
AlienVault OTX offers community-driven threat intelligence with 10 million+ indicators, accessible via Python SDKs. VirusTotal provides malware analysis and threat intelligence, with Python APIs for automated file and URL scanning. Recorded Future delivers real-time threat intelligence with Python SDKs for integration into security workflows. According to Gartner's threat intelligence market guide, threat intelligence spending will reach $4.2 billion in 2026.
Python is the processing language for threat intelligence: security analysts use Python with pandas and numpy to analyze threat data, matplotlib and seaborn to visualize trends, and scikit-learn to build machine learning models for threat prediction. Python's data science ecosystem makes it ideal for threat intelligence analytics.
Compliance and Governance: Security Mesh for Regulatory Requirements
Security mesh simplifies compliance with regulations like GDPR, HIPAA, PCI DSS, and SOC 2 by providing centralized policy management and audit trails. According to Gartner's compliance report, 61% of security mesh adopters report better compliance outcomes, with 54% lower audit costs due to automated evidence collection. AWS Audit Manager automates compliance evidence collection for AWS environments, with Python APIs for custom controls. Azure Policy enforces compliance policies across Azure resources, with Python SDKs for policy automation.
Vanta and Drata provide automated compliance monitoring for SOC 2, ISO 27001, and GDPR, with Python APIs for integration into security mesh. Lacework offers cloud security posture management (CSPM) with automated compliance checks, accessible via Python SDKs. According to Forrester's compliance automation report, compliance automation spending will reach $6.8 billion in 2026.
Python is the automation language for compliance: security teams use Python to collect compliance evidence, generate audit reports, and remediate policy violations. Python's integration with cloud platforms and security tools makes it the natural choice for compliance automation.
Conclusion: Security Mesh as the Future of Cybersecurity
Cybersecurity mesh architecture has reached 31% enterprise adoption in 2026, driven by the collapse of traditional perimeter security and the rise of remote work, multi-cloud, and zero trust requirements. Security mesh provides identity-centric protection, distributed policy enforcement, centralized orchestration, and multi-vendor interoperability, with 73% of adopters reporting reduced attack surface and 79% seeing improved visibility. Python has emerged as the automation language for security mesh, enabling security teams to orchestrate policies, integrate tools, process threat intelligence, and automate compliance across distributed environments. As security mesh adoption accelerates, Python will remain the bridge between security tools, cloud platforms, and security operations, enabling the next generation of adaptive, distributed cybersecurity.




